KringleCon 4: Four Calling Birds WriteUp - Printer Exploitation
Posted: Jan 14, 2022 | ~ 2 mins read time#ctf #kringlecon-2021 #cryptography
Objective: Printer Exploitation
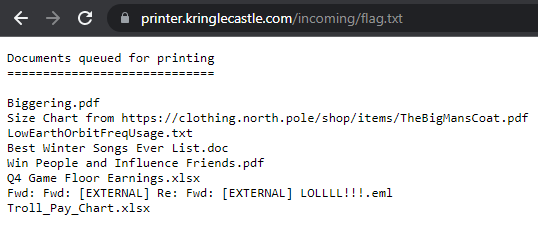
Investigate the stolen Kringle Castle printer. Get shell access to read the contents of /var/spool/printer.log. What is the name of the last file printed (with a .xlsx extension)?
Hint: There is the open directory printer.kringlecastle.com/incoming which is accessible without requiring authentication.
Navigating to the printer’s web GUI, there’s no place for input except on the Firmware Update page.
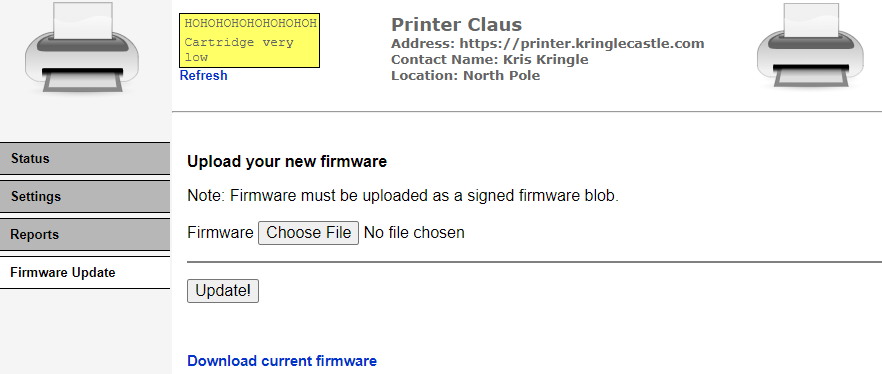
Out of curiousity, I created a test doc without any special formatting or code and uploaded it to see what would happen
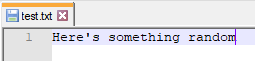
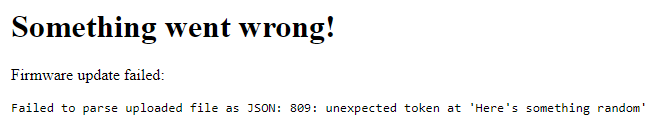
I then added JSON and tried again.
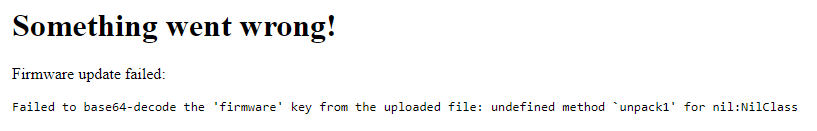
With that error code, I went down the rabbit hole of possibly finding a python exploit but that led nowhere. I then went back to the firmware page and noticed you could download the current version. Maybe this file could be used a template to get remote code execution?
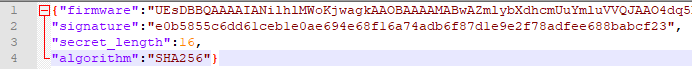
By uploading that firmware string into CyberChef, I could tell it was a base64 encoded zip archive containing a firmware.bin file.
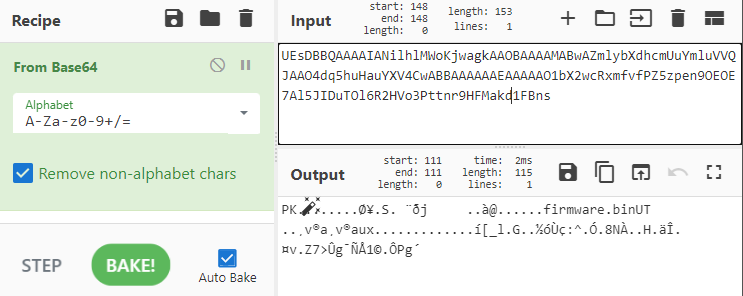
My initial thought was to create my own C program that copies the log file to the open directory, zip it up, base64 encode it, and make my own “firmware update”. Unfortunately, though, I didn’t have the secret key and couldn’t sign it properly.
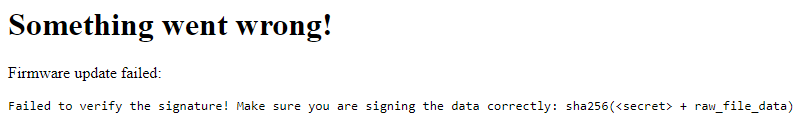
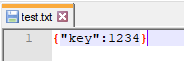
That’s when I looked up the hint provided for the challenge and read up on hash length extension attacks. Without the hint, the tipoff for this attack type was the error message that explains how to generate a signature: a SHA256 hash of the raw file data prepended with the secret. If I could add my C code to the end of the legitimate firmware update, I could generate an acceptable signature without knowing the secret!
Through trial and error, I learned the following:
- My C program had to be named
firmware.binor the attack would fail. - The order of creating the firmware string was add two
firmware.binfiles into the same archive and then base64 encode the file. Don’t zip and base64 encode each file individually.
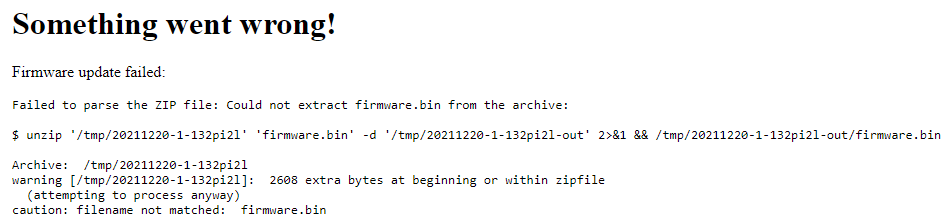
Once I got the file successfully uploaded, I switched over to the open directory to view the log file and find the last printed XLSX file.
To see my other writeups for this CTF, check out the tag #kringlecon-2021.
