KringleCon 4: Four Calling Birds WriteUp - Strace, Ltrace, Retrace
Posted: Jan 12, 2022 | ~ 1 min read time#ctf #kringlecon-2021 #reverse-engineering #linux
Here’s a writeup of another side quest that required some light reversing of an ELF binary.
Side Quest: Linux Process Investigation
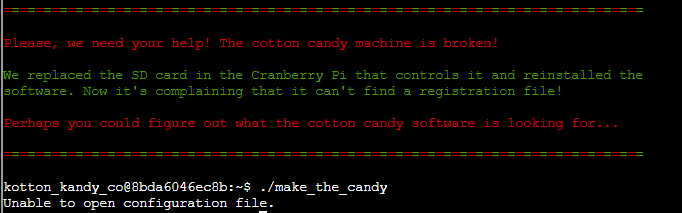
We’re given an ELF binary that seems to be missing a registration file. No other errors are shown so we’ll need to start tracing the process using a couple tools: strace and ltrace.
With strace, we can view the system calls. Special flags can filter the output but, to keep it basic, I ran it without any parameters.
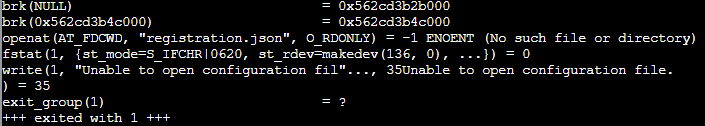
In the output, we can see the openat syscall for a registration.json file.
Just for kicks, I created an empty file named registration.json to see if it worked or if any useful errors could be found. But no such luck!
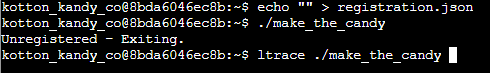
Syscalls can only get you so far so we’ll need to pull out ltrace for more information. With ltrace, we can view library calls. From this initial run, we can see the strstr function comparing the file contents with the expected value (in this case, the keyword Registration).
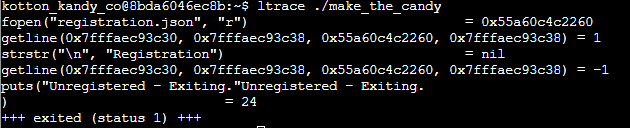
Now it’s just a process of running ltrace to see what values it expects and adding those values to the registration.json file.
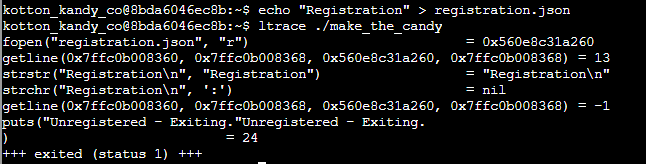
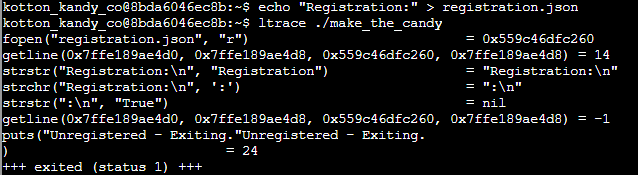
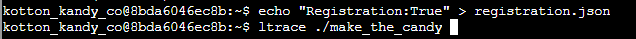
Unfortunately, I wasn’t able to get a screenshot of a successful run because, once you are able to run make_the_candy, ascii art starts to flow across the screen. However, to recap, the answer is to create the file registration.json with the contents
Registration:True
To see my other writeups for this CTF, check out the tag #kringlecon-2021.
