KringleCon 4: Four Calling Birds WriteUp - IPv6
Posted: Jan 12, 2022 | ~ 1 min read time#ctf #kringlecon-2021 #network
Side Quest: IPv6 Investigation
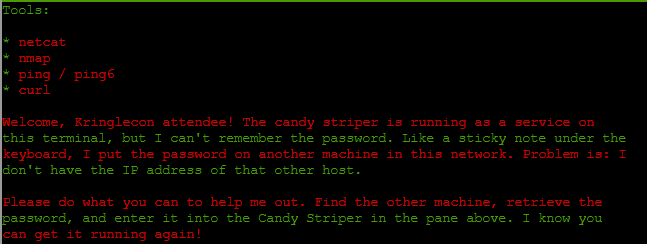
The methodology used for IPv4 will be the same for IPv6 - we just need to figure out the right tools.
Step 1: Enumerate hosts that are “up”
Normally, I would just run nmap across the subnet as a ping sweep across the subnet. However, with IPv6, the subnets are gigantic are scannin all available IP space is not realistic. So I checked the other available tools and noticed you can use ping6 to interrogate the all nodes multicast address to see live IPs on a subnet. An awesome in-depth explanation of IPv6 scanning can be found here.
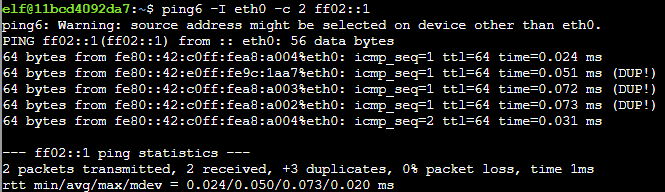
Step 2: Scan “up” hosts for open ports
Now that I got a list of live hosts, I then was able to use nmap to scan for open ports.
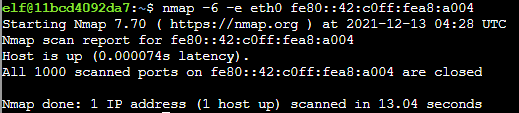
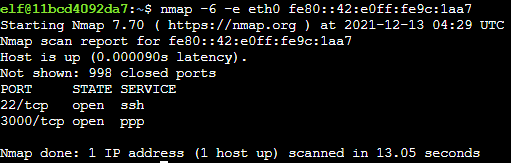
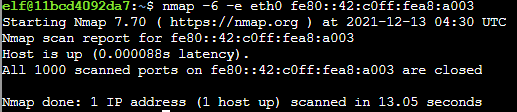

Step 3: Access available hosts via the open ports and profit
Since we have curl available to use, I focused on host #4 first and investigated port 80.
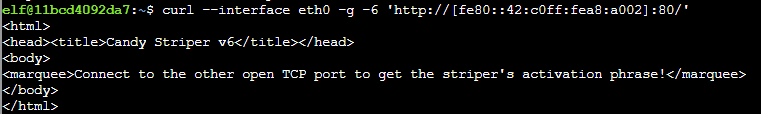
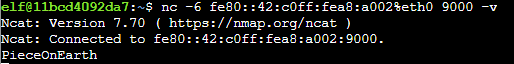
From there, I was able to run netcat against port 9000 and find the flag:
To see my other writeups for this CTF, check out the tag #kringlecon-2021.
