UTCTF 2021 WriteUp
Posted: Mar 17, 2021 | ~ 7 mins read time#ctf #cryptography #web #forensics #osint
This year, UTCTF hosted a wide range of challenges that included cryptography, forensics, reverse engineering, and web exploits. I focused mainly on forensics and cryptography while dabbling with the web puzzles.
I would definitely recommend this CTF to any skill level due to the variety not only of the categories but also the difficulty. Some of these challenges were very obvious and quick wins while others kept me up at night. The timespan lasting the whole weekend (Friday evening to Sunday evening) also gave me plenty of time to work on this without getting in the way of other weekend activities.
Cryptography
Small P Problems
My buddies Whitfield and Martin were trying to share a secret key between themselves, and I was able to eavesdrop on their conversation. I bet I could probably figure out their shared secret with a little math…
p = 69691
g = 1001
A = 17016
B = 47643
This puzzle uses the Diffie-Hellman key exchange algorithm. Basically, Alice has a private key a and Bob has a private key b. The pair agrees upon a pre-determined prime number p and integer g. To generate their public keys A and B, they must compute A = g^a (mod p) and B = g^b (mod p), respectively. The shared key is then defined as s = A^b (mod p) = s B^a (mod p). Our goal here is to find s. However, that requires knowledge of either a or b.
It took a lot of paper, ink, and googling for me to discover there is no shortcut. I tried using the Chinese Remainder Theorem and Fermat’s Little Theorem but had no luck. I was forced to create the python brute-force script below.
p = 69691
g = 1001
A = 17016
B = 47643
max_num = 1000000
i = 0
a_solved = 0
b_solved = 0
while i <= max_num:
if (A == g ** i % p and a_solved == 0):
print("a = ",i)
a_solved = 1
if (B == g ** i % p and b_solved == 0):
print("b = ",i)
b_solved = 1
if (a_solved == 0 or b_solved == 0):
i += 1
else:
i = max_num + 1
That script gave me the answers a = 12552 and b = 7919
After I found the private keys, I also found an online solver that provided all solutions: a = 12552 + 69690k and b = 7919 + 69690k for any integer k (Since this is using modular math, multiple answers can exist.)
This made the shared key s = A ^ b (mod p) = B ^ a (mod p) = 53919 and the solution utflag{53919}.
Illegal Prime
The NSA published the ciphertext from a one-time-pad. Since breaking one-time-pad is so easy, I did it for you.
To avoid legal trouble I can’t tell you the key. On an unrelated note I found this really cool prime number.
This problem only provided two variables:
c = 2f7f63b5e27343dcf750bf83fb4893fe3b20a87e81e6fb62c33d30
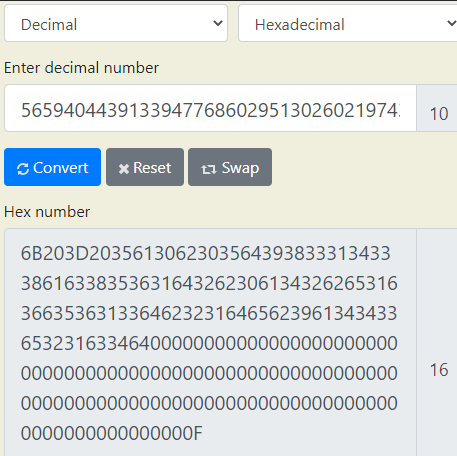
p = 56594044391339477686029513026021974392498922525513994709310909529135745009448534622250639333011770158535778535848522177601610597930145120019374953248865595853915254057748042248348224821499113613633807994411737092129239655022633988633736058693251230631716531822464530907151
This was an interesting puzzle and after reading about illegal primes, I fell down a deep rabbit hole of number theory. Coming back to the sunlight, I discovered converting the prime to hex and then to ASCII gave me the key.
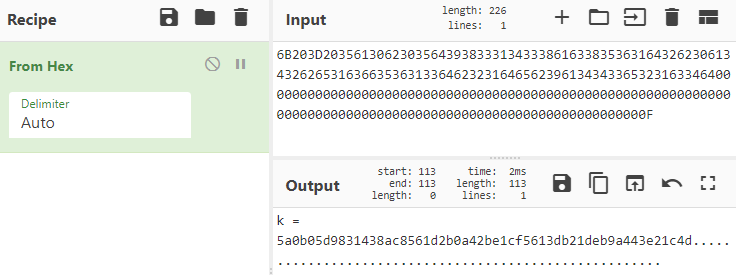
Rather than burn braincells creating my own one-time-pad decoder, I found a really nice online solver.
This gave the solution utflag{pr1m3_cr1m3s____!!!}
Web
Oinker
I found this cool more private alternative to twitter.
http://web2.utctf.live:5320/
Going to the webpage, I was shown a blank text box so I typed in a random string and hit submit.
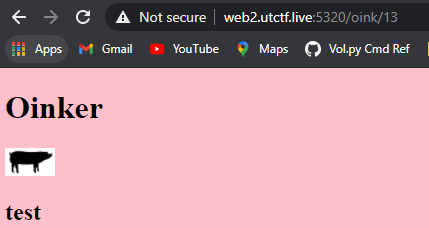
I noticed right away the URL had an index of 13. Out of curiosity, I checked if I was able to see other items such as 1, 2, 3, etc.
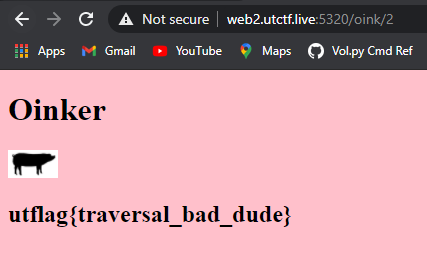
And then I saw the flag utflag{traversal_bad_dude}.
Source it!
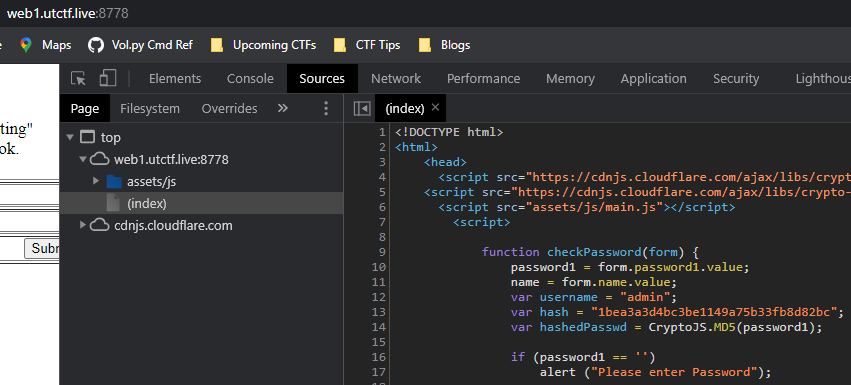
Can you see how this page handles authentication? http://web1.utctf.live:8778
From the source of the webpage, I found the MD5 hash of the correct password was hardcoded as well as the username being set to admin.
I’m partial to hashes.com for most of my CTF hash decoding needs. However, local programs such as HashCat or JohnTheRipper in Kali Linux are also super useful!
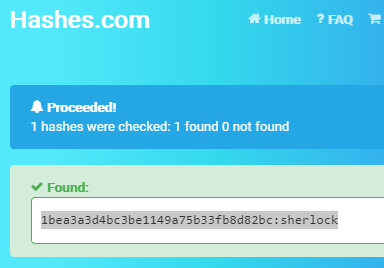
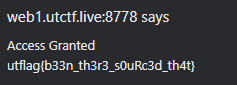
When I entered admin and sherlock, I got the flag utctf{b33n_th3r3_s0uRc3d_th4t}
Cutest Cookie Clicker Rip-Off
I built this awesome game based off of cookie clicker! Bet you’ll never beat my high score. Hehehe!
http://web1.utctf.live:4270
I’m greeted with a smiling cookie and prompted to click it as many times as I can within 30 seconds. If I can beat the high score, I’ll get the flag.
My first instinct was to create a script to automate the mouse clicks. The script worked but only got me to around 10,000.
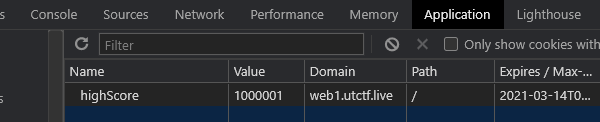
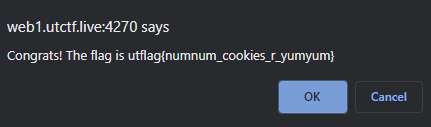
It was then I took a closer look at the website and noticed a cookie stored with my session to track my highest score. By simply editing that cookie to be greater than 1,000,000 got me the flag utflag{numnum_cookies_r_yumyum}.
Forensics
SHIFT
I just tried to download this flag, but it looks like the image got messed up in transit…
We’re given a distorted image that appears to have been slanted right.
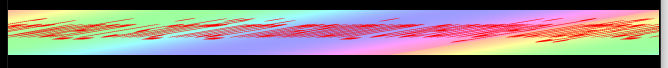
Using the shear tool in Gimp, we can see the flag utflag{not_when_i_shift_into_maximum_overdrive}

Doubly Deleted Data
We got a copy of an elusive hacker’s home partition and gave it to someone back in HQ to analyze for us. We think the hacker deleted the file with the flag, but before our agent could find it, they accidentally deleted the copy of the partition! Now we’ll never know what that flag was. :(
If you’re at all familiar with computers, you’ll know it can take *a lot* of effort to delete data from disk.
I initially tried to mount the image file with FTK Imager file but was unsuccessful as no file system was detected. I then took to using strings and grep against the image looking for the keyword utflag.
I came across two hits:
$ strings flash_drive.img | grep "utflag"
utflag{data_never_disappears}
utflag{data_never_disappears}
echo "utflag{d@t@_never_dis@ppe@rs}" > real_flag.txt
utflag{data_never_disappears}
echo "utflag{d@t@_never_dis@ppe@rs}" > real_flag.txt
echo "utflag{d@t@_never_dis@ppe@rs}" > real_flag.txt
utflag{data_never_disappears}
echo "utflag{d@t@_never_dis@ppe@rs}" > real_flag.txt
echo "utflag{d@t@_never_dis@ppe@rs}" > real_flag.txt
utflag{data_never_disappears}
echo "utflag{d@t@_never_dis@ppe@rs}" > real_flag.txt
Come to find out, the non-leet-speak version was a red herring and the official flag was utflag{d@t@_never_dis@ppe@rs}
OSINT Part 1
Can you find any OpSec vulnerabilities? http://misc.utctf.live:8756/
The contact information stood out the most - especially the new intern’s information.
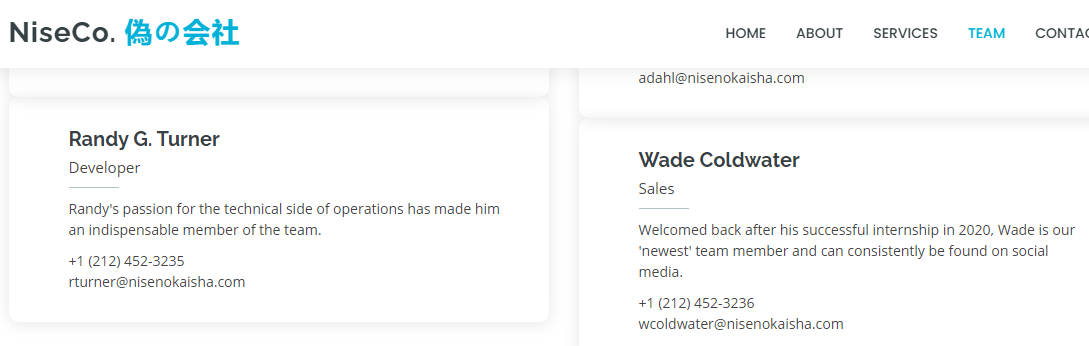
A Twitter hit appeared for the intern’s name!
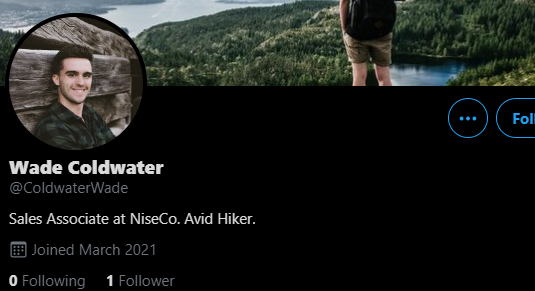
Looking through his recent tweets, I found his work badge with the flag utflag{g0t_y0ur_b4dg3}.

OSINT Part 2
Find the origins of the linked file found in part 1.
On Wade’s twitter, there was a Google drive with an image.
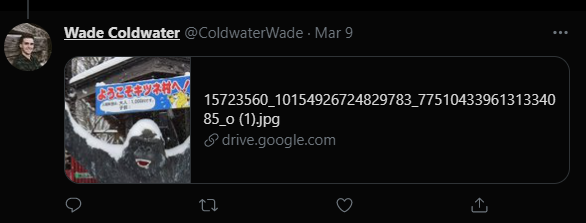
Downloading the file, I was able to do a reverse image search via Google to find the blog below with the matching file.
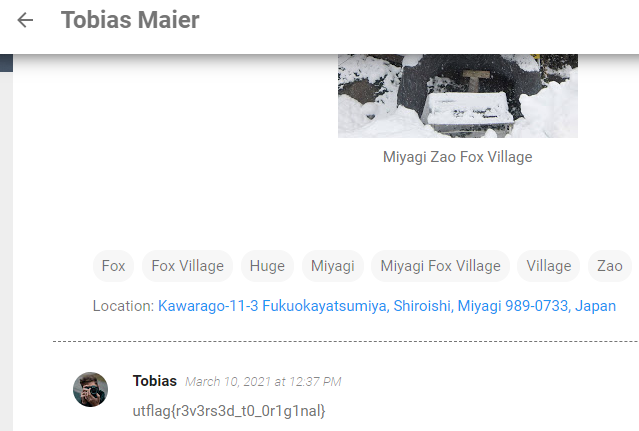
This gave me the flag utflag{r3v3rs3d_t0_0r1g1nal}.

